Hacker Stickers
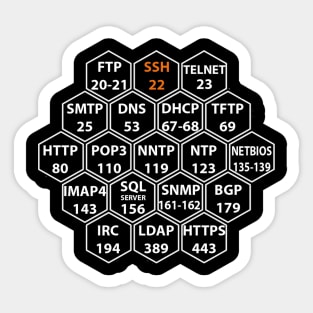
Description: TCP port 21 — FTP (File Transfer Protocol) TCP port 22 — SSH (Secure Shell) TCP port 23 — Telnet TCP port 25 — SMTP (Simple Mail Transfer Protocol) TCP and UDP port 53 — DNS (Domain Name System) TCP port 443 — HTTP (Hypertext Transport Protocol) and HTTPS (HTTP over SSL) TCP port 110 — POP3 (Post Office Protocol version 3) TCP and UDP port 135 — Windows RPC TCP and UDP ports 137–139 — Windows NetBIOS over TCP/IP

Description: Proudly display your ethical hacker side with this "I Hack For Good" t-shirt. Perfect for cybersecurity professionals, tech enthusiasts, or anyone in the white hat hacking community, this shirt celebrates the positive impact of hacking for security. With its bold and straightforward message, it's a fun and empowering tee for those who are committed to protecting the digital world.
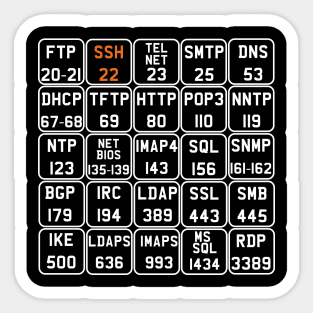
Description: TCP port 21 — FTP (File Transfer Protocol) TCP port 22 — SSH (Secure Shell) TCP port 23 — Telnet TCP port 25 — SMTP (Simple Mail Transfer Protocol) TCP and UDP port 53 — DNS (Domain Name System) TCP port 443 — HTTP (Hypertext Transport Protocol) and HTTPS (HTTP over SSL) TCP port 110 — POP3 (Post Office Protocol version 3) TCP and UDP port 135 — Windows RPC TCP and UDP ports 137–139 — Windows NetBIOS over TCP/IP

Description: In the world of IT hackers are seen as computer experts with operating system, networking and programming skills who use their power to solve problems for good or evil. Do you consider yourself a hacker? Then this design is for you. The design shows the word hacker in Traditional Chinese characters in a lucid green with pink stars shining through. A cool and mysterious design for work, hacking events and tech conferences, where computer hacking geeks and nerds meet.
Hacker in Chinese Green/Pink Space Computer Hacker Design Sticker
by Geeksta - Cool and Funny IT Geek Designs
$3.25

Description: Nerd shirt for hackers Unleash your inner cyberpunk with our unique Hacker Cat design. Featuring a sleek black cat donning a hoodie, this design is perfect for anyone who wants to express their love for technology and hacking culture. Show off your edgy style and love for all things cyber with our Hacker Cat design today!

Description: A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination.

Description: FANCY BEARS' Hack Team. A computer hacker is any skilled computer expert that uses their technical knowledge to overcome a problem. While "hacker" can refer to any skilled computer programmer, the term has become associated in popular culture with a "security hacker", someone who, with their technical knowledge, uses bugs or exploits to break into computer systems.
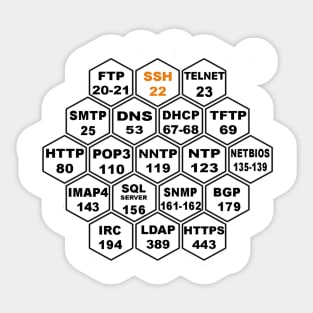
Description: TCP port 21 — FTP (File Transfer Protocol) TCP port 22 — SSH (Secure Shell) TCP port 23 — Telnet TCP port 25 — SMTP (Simple Mail Transfer Protocol) TCP and UDP port 53 — DNS (Domain Name System) TCP port 443 — HTTP (Hypertext Transport Protocol) and HTTPS (HTTP over SSL) TCP port 110 — POP3 (Post Office Protocol version 3) TCP and UDP port 135 — Windows RPC TCP and UDP ports 137–139 — Windows NetBIOS over TCP/IP

Description: A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination.

Description: The terms “deep web” and “dark web” are sometimes used interchangeably, but they are not the same. Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google. Deep web content includes anything behind a paywall or requires sign-in credentials. It also includes any content that its owners have blocked web crawlers from indexing. Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Estimates place the size of the deep web at between 96% and 99% of the internet. Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”.
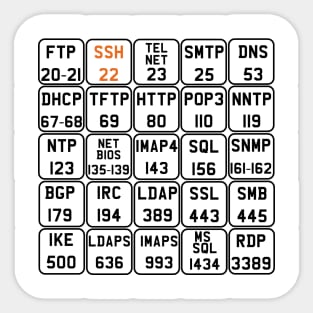
Description: TCP port 21 — FTP (File Transfer Protocol) TCP port 22 — SSH (Secure Shell) TCP port 23 — Telnet TCP port 25 — SMTP (Simple Mail Transfer Protocol) TCP and UDP port 53 — DNS (Domain Name System) TCP port 443 — HTTP (Hypertext Transport Protocol) and HTTPS (HTTP over SSL) TCP port 110 — POP3 (Post Office Protocol version 3) TCP and UDP port 135 — Windows RPC TCP and UDP ports 137–139 — Windows NetBIOS over TCP/IP

Description: A white hat is an ethical computer hacker, or a computer security expert, who specializes in penetration testing and in other testing methodologies that ensures the security of an organization's information systems. Ethical hacking is a term meant to imply a broader category than just penetration testing